Smart AppLock is an AppLocker or App Protector that will lock and protect apps using a password or pattern and fingerprint. Lock Facebook, Whatsapp, Gallery apps with password and prevent the apps from being exposed by snooper! Online data transfer from mobile to pc. Version 7.6.0 & 7.7.0. changed 'Screen/Rotation Lock' feature - screen orientation can be individually set when. AppLock allows you to lock apps and protect your apps using Pattern, Pin, Fingerprint and crash screen. Features - Lock Apps / App Locker AppLock allows you to lock apps like gallery, message apps, social apps and email apps with fingerprint, pin, pattern and crash screen. https://lcxsg.over-blog.com/2021/01/can-i-install-el-capitan.html. Vegas crest casino no deposit bonus codes 2016. Capture Intruder Picture If someone tries to open locked apps with wrong password, AppLock.
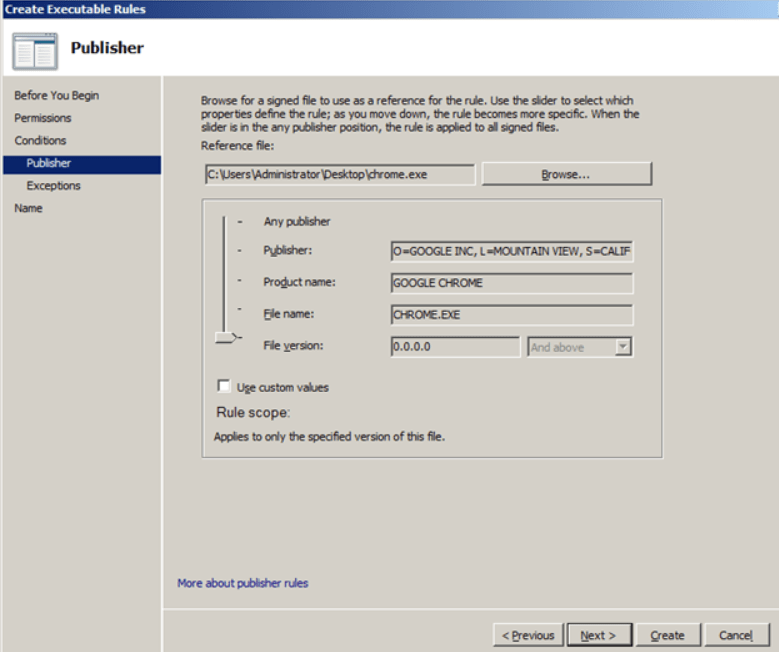
Some IT departments choose to control which applications users can run. Sometimes, administratorssimply block specific applications that are known to be problematic. However, clientsecurity benefits more when administrators block all applications that IT has not approved.
The benefits of restricting users from running applications that are not approved can beimmense. First, the risk of malware is significantly reduced, because Windows would preventusers from running the malware application because it had not been approved by IT. Second,compatibility problems are reduced, because users can only run approved versions of applications.Finally, user productivity is increased by eliminating the possibility that users couldrun games or other applications that might take time away from their work.
Restricting users from running applications does have significant costs, however, andfor many organizations, those costs outweigh the benefits. IT has to test each applicationand create a rule that allows users to run it. Inevitably, users will be prevented from runninglegitimate applications, which can reduce their productivity while they wait for IT to approvea new application. Sometimes, users will choose to work around IT by running applications onnon-IT computers. Each time an application is updated, IT needs to again test and approvethe application.
Windows 7 includes AppLocker, which is an update to Software Restriction Policies, a featurein earlier versions of Windows. With Software Restriction Policies, IT professionals couldcreate rules such as 'Trust all content signed by Microsoft,' 'Trust this single executable file,'or 'Trust the file at this path.' With AppLocker, IT professionals can create more refined rulesbased on an application's metadata, such as 'Trust Microsoft Office if it is signed and the versionis greater than 12.0.0.0.' Additionally, AppLocker rules can be assigned on a per-groupand per-user basis.
Table lists the differences between Software Restriction Policies and AppLocker
Software Restriction Policies Compared to AppLocker
| Feature | Software Restriction Policies | Applocker |
| Conditions | Hash, path, certificate, registry path, and Internet zone | Hash, path, and publisher |
| Rule scope | All users | All users, or specific users and groups |
| Audit-only mode | No | Yes |
| Automatically generate rules | No | Yes |
| Policy import and export No | No | Yes |
| Windows PowerShell support | No | Yes |
| Custom error messages | No | Yes |
AppLocker is available only in Windows 7 Enterprise and Windows 7 Ultimate Editions. Youcan use Windows 7 Professional Edition to create AppLocker rules, but the rules will not beenforced on the computer running Windows 7 Professional. You must configure the ApplicationIdentity service to start for Windows 7 to apply AppLocker rules; by default, it is configured tostart manually.
Crosscode 1 03 2 download free. The sections that follow provide more detailed information about how to configure, test,and manage AppLocker.
In this tutorial:
AppLocker is an application whitelisting technology introduced with Microsoft'sWindows 7 operating system. It allows restricting which programs users can execute based on the program's path, publisher, or hash,[1] and in an enterprise can be configured via Group Policy.
Summary
Windows AppLocker allows administrators to control which executable files are denied or allowed to execute. With AppLocker, administrators are able to create rules based on file names, publishers or file location that will allow certain files to execute. Unlike the earlier Software Restriction Policies, which was originally available for Windows XP and Windows Server 2003,[2] Power save 3 70. AppLocker rules can apply to individuals or groups. Policies are used to group users into different enforcement levels. For example, some users can be added to an 'audit' policy that will allow administrators to see the rule violations before moving that user to a higher enforcement level.
Some IT departments choose to control which applications users can run. Sometimes, administratorssimply block specific applications that are known to be problematic. However, clientsecurity benefits more when administrators block all applications that IT has not approved.
The benefits of restricting users from running applications that are not approved can beimmense. First, the risk of malware is significantly reduced, because Windows would preventusers from running the malware application because it had not been approved by IT. Second,compatibility problems are reduced, because users can only run approved versions of applications.Finally, user productivity is increased by eliminating the possibility that users couldrun games or other applications that might take time away from their work.
Restricting users from running applications does have significant costs, however, andfor many organizations, those costs outweigh the benefits. IT has to test each applicationand create a rule that allows users to run it. Inevitably, users will be prevented from runninglegitimate applications, which can reduce their productivity while they wait for IT to approvea new application. Sometimes, users will choose to work around IT by running applications onnon-IT computers. Each time an application is updated, IT needs to again test and approvethe application.
Windows 7 includes AppLocker, which is an update to Software Restriction Policies, a featurein earlier versions of Windows. With Software Restriction Policies, IT professionals couldcreate rules such as 'Trust all content signed by Microsoft,' 'Trust this single executable file,'or 'Trust the file at this path.' With AppLocker, IT professionals can create more refined rulesbased on an application's metadata, such as 'Trust Microsoft Office if it is signed and the versionis greater than 12.0.0.0.' Additionally, AppLocker rules can be assigned on a per-groupand per-user basis.
Table lists the differences between Software Restriction Policies and AppLocker
Software Restriction Policies Compared to AppLocker
| Feature | Software Restriction Policies | Applocker |
| Conditions | Hash, path, certificate, registry path, and Internet zone | Hash, path, and publisher |
| Rule scope | All users | All users, or specific users and groups |
| Audit-only mode | No | Yes |
| Automatically generate rules | No | Yes |
| Policy import and export No | No | Yes |
| Windows PowerShell support | No | Yes |
| Custom error messages | No | Yes |
AppLocker is available only in Windows 7 Enterprise and Windows 7 Ultimate Editions. Youcan use Windows 7 Professional Edition to create AppLocker rules, but the rules will not beenforced on the computer running Windows 7 Professional. You must configure the ApplicationIdentity service to start for Windows 7 to apply AppLocker rules; by default, it is configured tostart manually.
Crosscode 1 03 2 download free. The sections that follow provide more detailed information about how to configure, test,and manage AppLocker.
In this tutorial:
AppLocker is an application whitelisting technology introduced with Microsoft'sWindows 7 operating system. It allows restricting which programs users can execute based on the program's path, publisher, or hash,[1] and in an enterprise can be configured via Group Policy.
Summary
Windows AppLocker allows administrators to control which executable files are denied or allowed to execute. With AppLocker, administrators are able to create rules based on file names, publishers or file location that will allow certain files to execute. Unlike the earlier Software Restriction Policies, which was originally available for Windows XP and Windows Server 2003,[2] Power save 3 70. AppLocker rules can apply to individuals or groups. Policies are used to group users into different enforcement levels. For example, some users can be added to an 'audit' policy that will allow administrators to see the rule violations before moving that user to a higher enforcement level.
AppLocker availability charts
| Starter | Home Basic | Home Premium | Professional | Enterprise | Ultimate |
|---|---|---|---|---|---|
| No | No | No | Create policies, but cannot enforce | Create and enforce policies | Create and enforce policies |
| RT | (Core) | Pro | Enterprise |
|---|---|---|---|
| No | No | No | Yes |
| Home | Pro | Enterprise | Education |
|---|---|---|---|
| No | No | Yes | Yes |
Bypass techniques
There are several generic techniques for bypassing AppLocker:
Applocker 2 7 0 945
- Writing an unapproved program to a whitelisted location.
- Using a whitelisted program as a delegate to launch an unapproved program.[7][8][9][10]
- Hijacking the DLLs loaded by a trusted application in an untrusted directory.[11]
References
Applocker 2 7 0 9 Inches
- ^'AppLocker'. Microsoft TechNet. Microsoft. Retrieved 23 August 2012.
- ^'Using Software Restriction Policies to Protect Against Unauthorized Software'. Microsoft TechNet. Microsoft. Retrieved 27 July 2017.
- ^'Windows Versions That Support AppLocker'. Microsoft. Retrieved 27 July 2017.
- ^Visser, Erwin (18 April 2012). 'Introducing Windows 8 Enterprise and Enhanced Software Assurance for Today's Modern Workforce'. Windows for your Business. Microsoft. Retrieved 22 November 2012.
- ^Dudau, Vlad (10 June 2015). 'Microsoft shows OEMs how to market Windows 10; talks features and SKUs'. Neowin. Neowin LLC. Retrieved 19 June 2015.
- ^'Find out which Windows is right for you'. Microsoft. Microsoft Inc. Retrieved 2 July 2015.
- ^'AppLocker Bypass – InstallUtil'. Penetration Testing Lab. Retrieved 27 July 2017.
- ^'AppLocker Bypass Techniques'. Evi1cg's blog. Retrieved 27 July 2017.
- ^'How to Bypass Windows AppLocker'. Hacking Tutorial. Retrieved 27 July 2017.
- ^'caseysmithrc/gethelp.cs'. Github Gist. Retrieved 14 May 2019.
- ^'Bypassing Application Whitelisting'. CERT/CC Blog. Retrieved 27 July 2017.
